Published
- 4 min read
Enhancing Web Application Security with Cloudflare Access: A Comprehensive Guide

Introduction
The rise of the digital era has shifted the need for a different kind of security. As web applications become increasingly central to businesses, the focus on their security has never been more significant.
Today, we’re focusing on how Cloudflare Access can serve as a robust security solution for your web applications, particularly during the development and preview stages.
Cloudflare Access, a modern security solution, offers a fresh approach to secure hybrid work. It is efficient and secure, an excellent alternative to traditional VPNs. Its applications span from accelerating mergers and acquisitions and providing fast access to contractors and developers, to offering phishing-resistant multi-factor authentication.
This article aims to provide a comprehensive guide on restricting access using Cloudflare Access. We’ll provide step-by-step procedures and relevant coding examples to ensure you can implement these measures effectively.
Cloudflare Access: A New Era of Web Security
The Need for Enhanced Security
With the increase in remote working and hybrid work models, securing sensitive data and internal resources has become an essential aspect of business operations. Traditional security measures like VPNs no longer suffice. This is where Cloudflare Access steps in.
What is Cloudflare Access?
Cloudflare Access is a security feature that provides secure, fast, and seamless access to internal applications without the need for a VPN. It provides a secure connection between users and the internet, protecting your web applications from threats.
Key Use Cases of Cloudflare Access
Cloudflare Access can be used in various scenarios, including:
- VPN replacement: Access offers a safer and faster alternative to traditional VPNs, enhancing security and user experience.
- Accelerating mergers and acquisitions: It can integrate with multiple identity providers (IdPs) and provide per-app internal access during M&As.
- Contractor access: Cloudflare Access can authenticate third-party users such as contractors with clientless options and social IdPs.
- Developer access: It allows technical users to securely access critical infrastructure without performance tradeoffs.
- Phishing-resistant MFA: Cloudflare Access allows the rollout of strong authentication like FIDO2-compliant security keys.
Restricting Access with Cloudflare: Step-by-Step Guide
Setting up Cloudflare Access
Go to the Cloudflare dashboard and navigate to the Zero Trust tab.
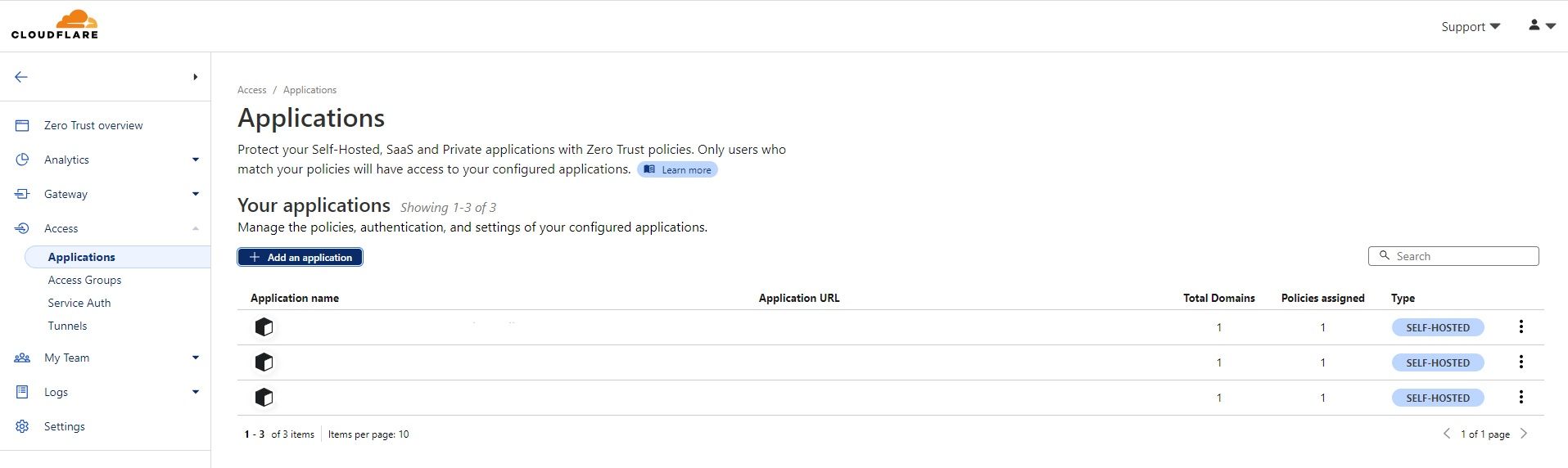
It would take a few seconds to get the Zero Trust dashboard. Then, go to Access and select Applications. Click on Add application.
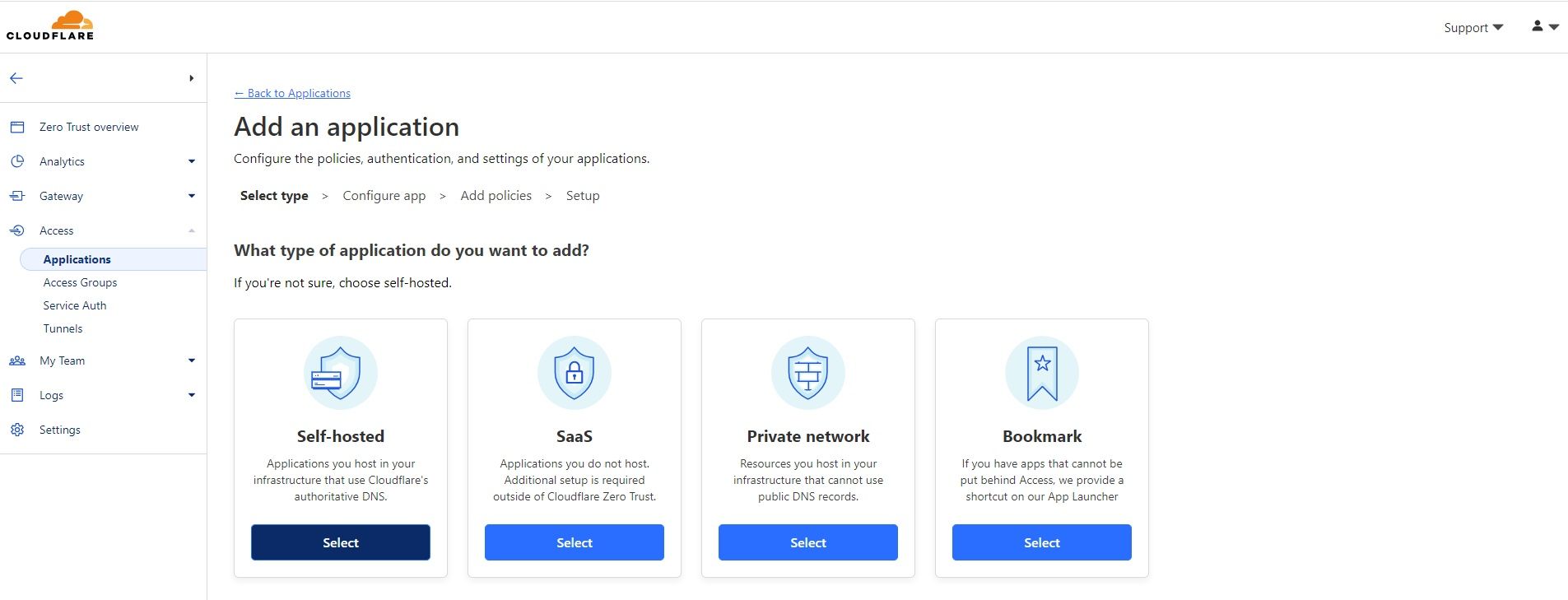
There are a few options that you can enable Access for. For this tutorial, we will be using the self-hosted application.
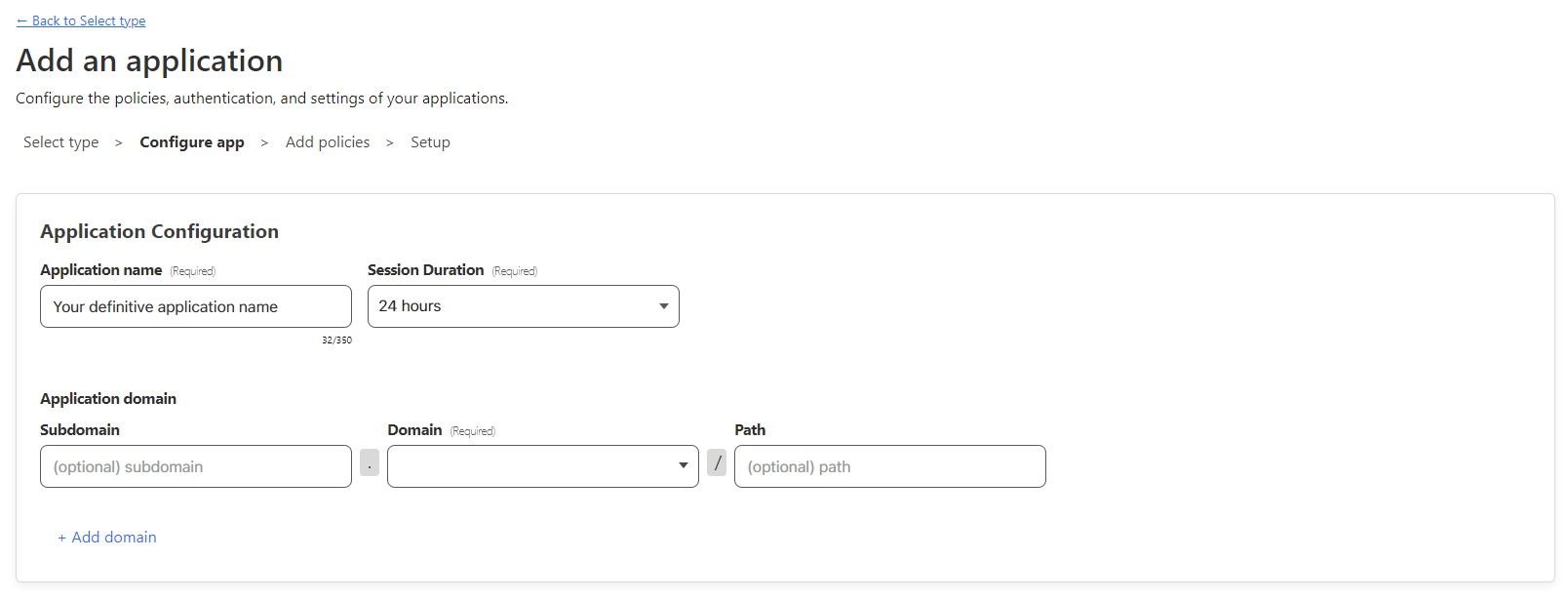
Now, we need to give a descriptive name to this application and decide the duration of the Access session. Also, we need to define the application’s domain.
Note, the domain must be on Cloudflare.
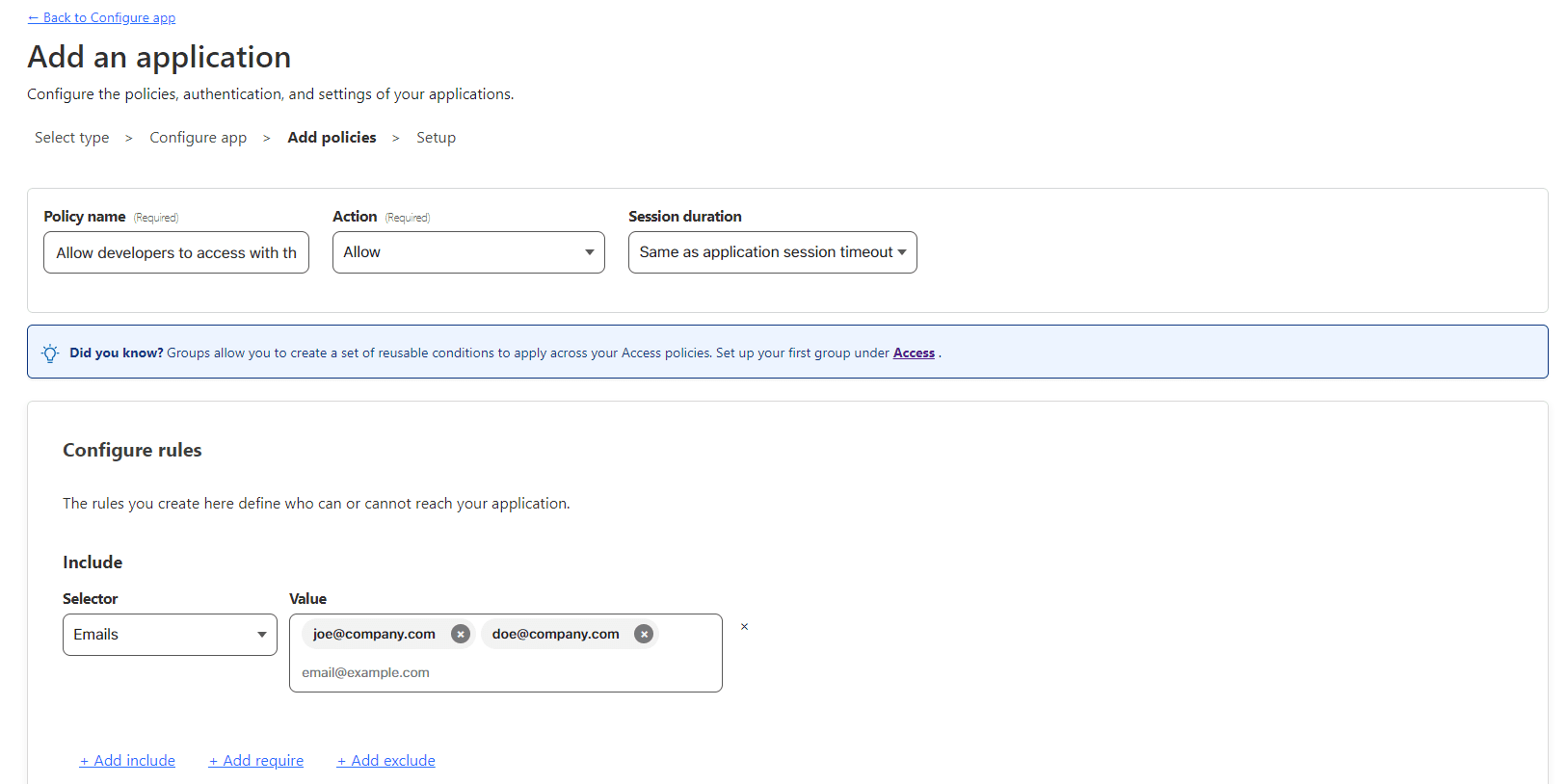
Define the policies you would like to enforce.
For this example, I will allow a set of emails to obtain access codes and access the application. There are many other options too. You can decide according to your needs.
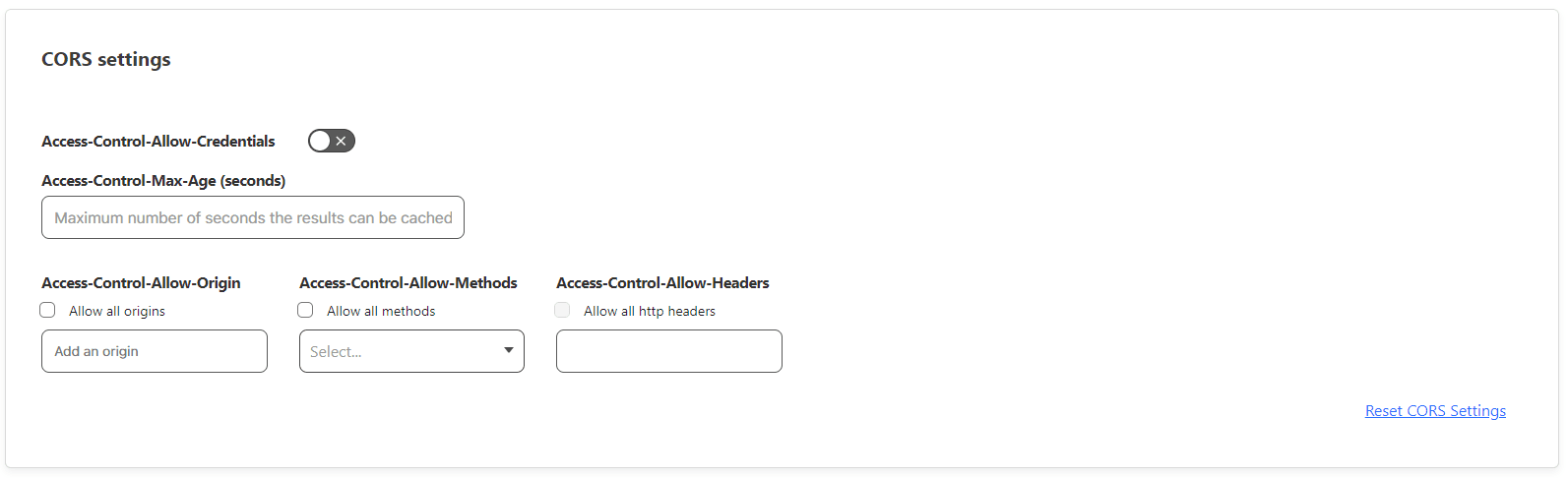
Also, we can define some extra settings.
Like, CORS settings:
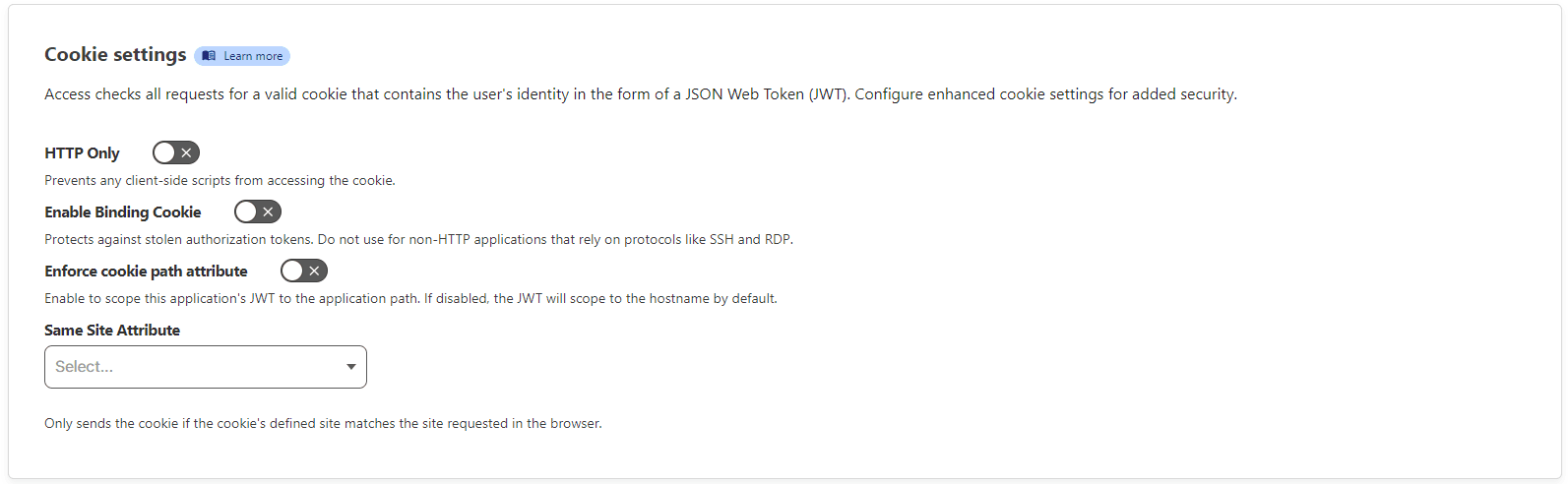
Cookie settings:
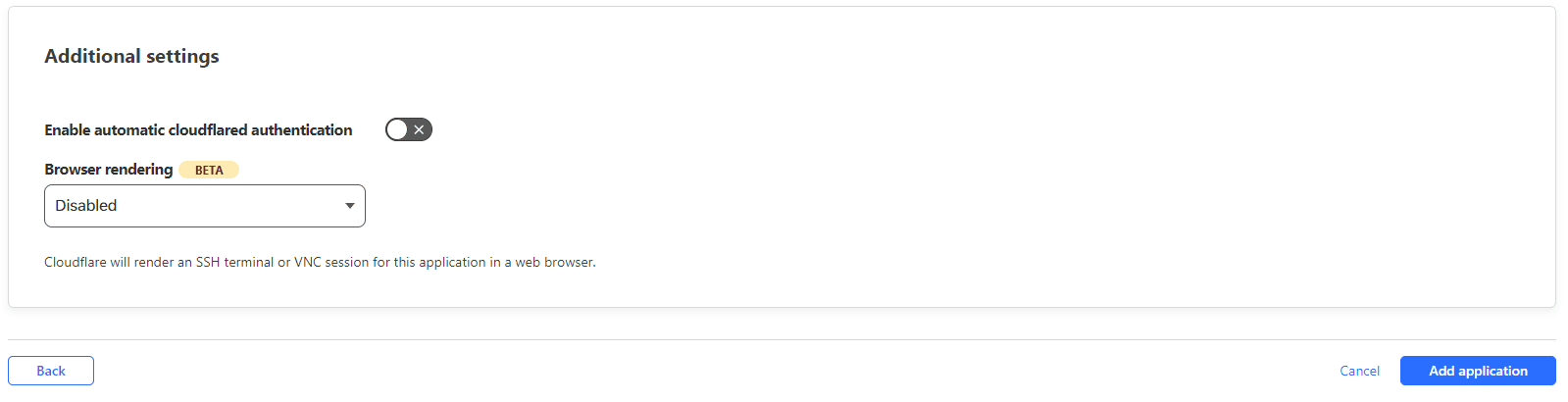
And finally, add the application.
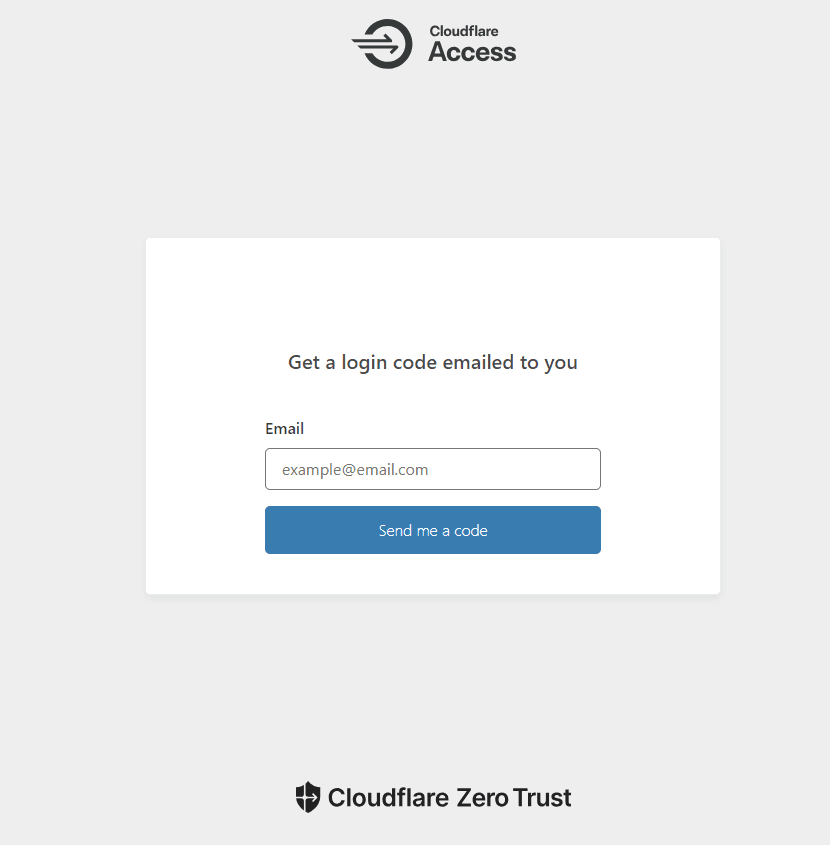
Now, visiting the application’s domain should display the Access login page.
Remember, we defined [email protected] and [email protected] email addresses on the policy to access the application. If you enter one of those addresses, it will get a code.
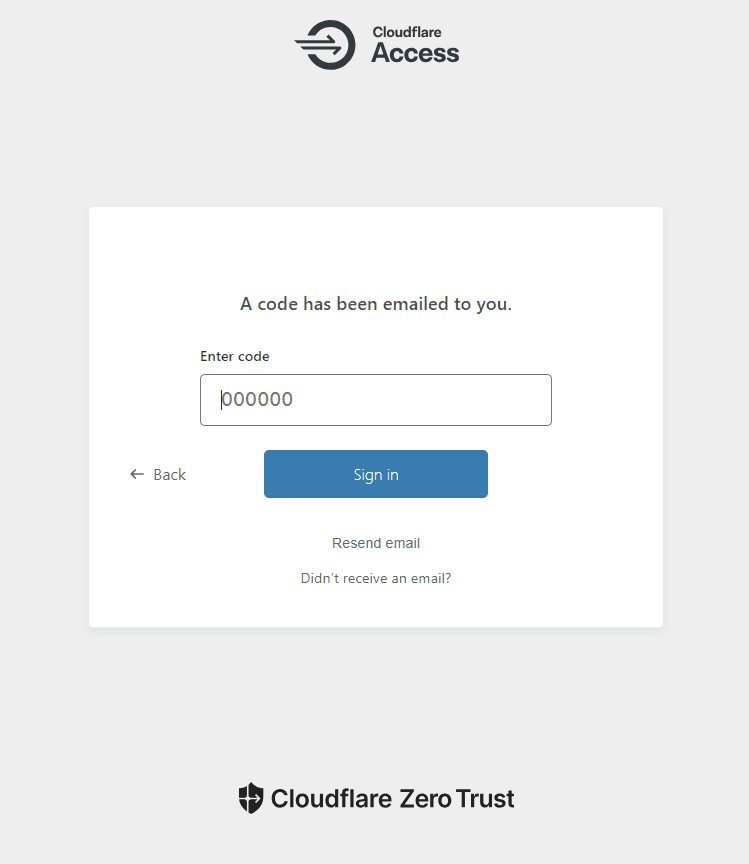
Finally, enter the code and securely access the application.
A note, even if you do not enter one of the defined email addresses on the previous screen, it still will show as it sent the code. This is a default security measure taken by Cloudflare.
Frequently Asked Questions
What is Cloudflare Access?
Cloudflare Access is a security feature that provides secure, fast, and seamless access to internal applications without the need for a VPN.
How does Cloudflare Access enhance security?
Cloudflare Access offers enhanced security by providing a secure connection between users and the internet, effectively protecting your web applications from threats by establishing a secure connection between users and the internet.
What are some use cases for Cloudflare Access?
Some of the primary use cases for Cloudflare Access include its use as a VPN replacement, accelerating mergers and acquisitions, providing secure access for contractors and developers, and rolling out phishing-resistant multi-factor authentication.
Conclusion
Web application security is an ongoing challenge for organizations of all sizes. With the ever-evolving threat landscape, it’s essential to equip ourselves with robust and reliable security tools. Cloudflare Access represents one such powerful tool in the modern security arsenal, offering secure and fast access to web applications at various stages of their lifecycle.
With its varied use cases, Cloudflare Access helps streamline operations without compromising security. By integrating Cloudflare Access into your security strategy, you can ensure that your applications are protected, keeping your data safe and your operations running smoothly.
Remember, security is not a one-time setup but a continuous process. Stay vigilant, stay updated, and most importantly, stay secure.